Kaspersky
Recently the US government (the DHS to be exact) issued an order to all federal agencies to remove Kaspersky from their systems. They were given 90 days to do so.
The vast majority of us probably have no clear idea of what this order means let alone its consequential implications. Some federal agencies have networks with hundreds of thousands of computers. If they are using Kaspersky, they will first need to identify a replacement. Assuming they rush into things, and put it up for bid quickly, I give them at least 30 days to be ready to start. And frankly, I am being very conservative. That leaves them with 60 days to replace the AV on 100,000 computers. I insist on ‘replace’ because typically you can’t simply install another AV and move on. In most cases, you need to remove the existing one first, then install the replacement. I think it is quite clear that the task is daunting, and this order reveals once more the typical incompetence at certain levels of the chain of command, which reflect negatively on those below.
However, this is not the issue I want to investigate here.
Suspicions against foreign products is not new. President Obama accused Huawei of inserting spying software into their switches. As far as I know, none were ever actually found, and it later turned out that the move was politically motivated (maybe to give AT&T a little boost in its losing battle against a new communication giant dominating the global markets).

Ironically, the only backdoors found so far into legitimate products, have always involved US companies. Seems to be a pattern – we accuse other countries, but at the end of the day, we are the ones who must do some explaining.
As for Kaspersky Labs, Mr. Kaspersky himself has repeatedly said he’s willing to open his code for the international community to investigate these claims of trojan horses and spying software embedded into it. Now the DHS is saying that its decision is based mostly on “open source” information. However, such information has been kept classified (so much for open source) and has not been explained in details. In other words, the DHS is asking us to trust and believe, without really providing any proof. How is that for blind faith?
On his side, Mr. Kaspersky is, of course, pushing back, and hard. While it is true that he has a past with the KGB, it is also true that the US is his company’s largest market, and losing it would drastically reduce Kaspersky’s influence and presence in the AV space. The US represents around 2/3 of Kaspersky Labs’ entire revenue. In fact, we could very well witness the complete downfall of the company altogether, especially if all these allegations turn out to be true. Which makes you wonder – would the man really risk his fortune this way? Does he even have a choice? Is there any basis to all this? I don’t think we can answer these questions, unless the DHS tells us exactly what they are basing these accusations on.

However, given current political atmospheres surrounding relationships between the US and Russia (their interference in our elections, all those investigations involving the WH or individuals somehow tied to it), one must wonder if this isn’t all merely a political stunt. I can’t personally attest that it is or it isn’t. But I do have to put it out there; as I am sure many have already done as well.
Articles on the NYT have reported that the Israelis were able to hack into Kaspersky’s network, and install key loggers and take screenshots of what their users were doing. Allegedly they passed this information to the US, which finally acted upon it now by deciding to pull the plug on Kaspersky. The article does specify that this could well have been done without Mr Kaspersky’s knowledge; after all any of his employees could have done this without anyone being the wiser.
Another article though, from PC Magazine, tells a different story. They feel that these claims are still unsubstantiated and therefore, continue to recommend Kaspersky, especially for the private sector, since the current AV industry’s environment does not really leave much choice – Kaspersky is, and remains, “simply the best”.
However, since this is a technical and not a political piece, we need to also analyze the network security consequences of such a decision – aside from the horrible panic that must be spreading like wildfire at the various agencies affected by this order, of course.
Look at the 2 links below:
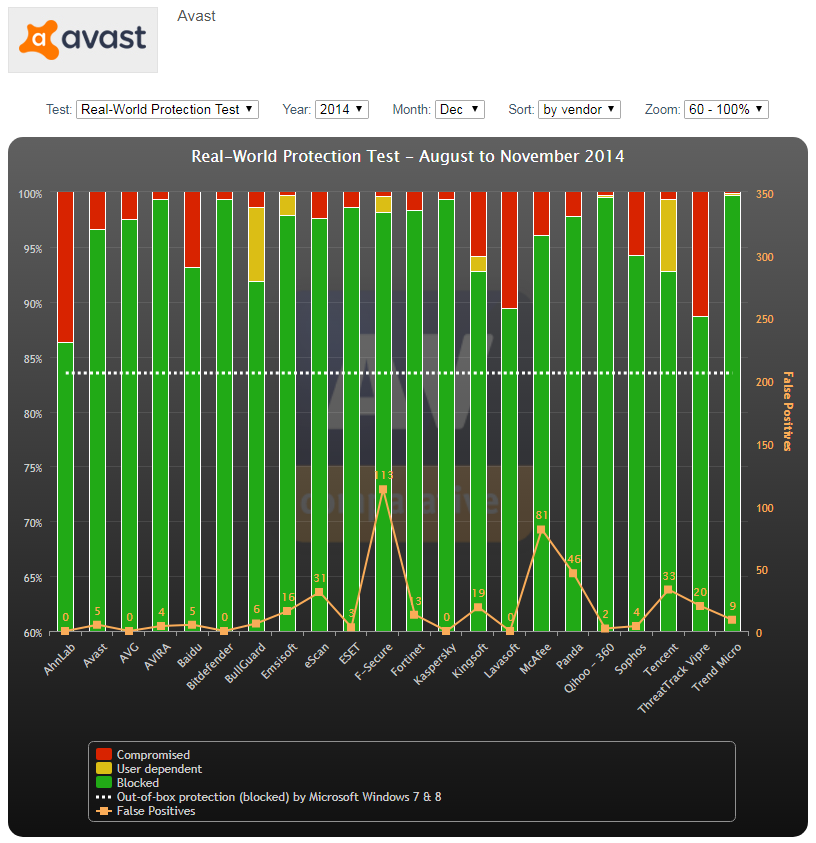
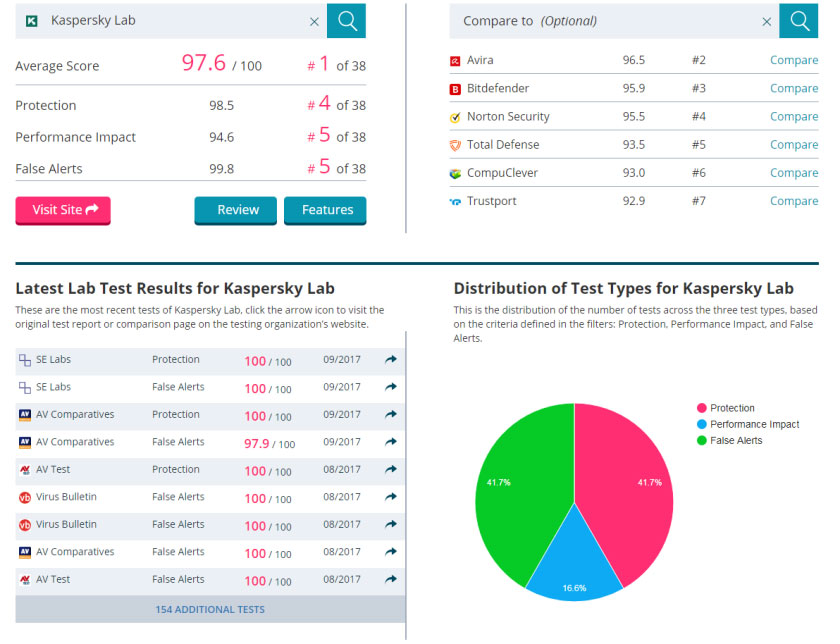
Once there, play with the dates as well. You will notice one consistent thing in all of them – Kaspersky is always the first. It is always the one that catches everything, and has no false positives. That is amazing performance, and no other AV company has been able to keep up, with a possible contender appearing to be Bitdefender. Symantec scores well sometimes, but it has high false positives, and is inconsistent.
So, what choice are these federal agencies to make now?
Where should they go?

If they choose an AV made in the US, they are lowering their security posture and increasing the number of false positives. As if they haven’t already had enough issues in the past years, with breaches and loss of data. If they select a foreign one, what if the DHS decides to ban that product as well in the future?
For example, Bitdefender is from Romania; their headquarters are in Bucharest. OK, Romania is part of the EU, so no big deal, right? Wrong. They are also an ex-USSR nation. Who knows, some ghosts from the past might still be lurking. Sarcasm aside, it is not too farfetched to assume that other countries could also fall under the ire of this temperamental administration, apparently intent on picking fights with anyone they can. Perhaps the federal agencies should simply pick a US based company, and accept the fact that they will have more viruses, more data breaches to report, and, well, just suck it up.
For all the reasons expressed so far, I feel it is fair to say that this is an issue only for federal agencies, or for anyone who might have something that the Russian government might want to spy upon. Yes, if you are the DNC HQ, you may want to err on the side of caution, and not use Kaspersky. Just in case those allegations prove true, and come back to haunt you. But if you are in the private sector, even if you are a bank, a small bank maybe, what information does your company have that the Russian government might want to steal? And for what purpose? In such case maybe, just maybe, you should ignore all the political fuss, and make a choice based on technical reasons.

At Network Box, we are testing other AV products. We understand that our clients in the US, even in the private sector, are concerned by all this fracas surrounding Kaspersky Labs, and are asking for alternatives. Though the DHS cannot enforce any decision on the private sector, we have already seen banking examiners ‘demand’ Kaspersky be removed. However, we will not be doing this. We firmly believe in the superiority of Kaspersky as an AV product, and have no reason to not trust it. We will, however, introduce options, and present clients with a dual offer. Ultimately, it will be up to them to decide if they want the best AV product available in the market, or not.
Once the client’s decision has been made, OEM negotiations have been settled, and development is under way, we will make a public announcement as to which product we have selected, and difference in pricing, if any.